Blockchain technology is revolutionizing the way we secure digital transactions, and at its core lies the concept of hashing. But how does a hash help secure blockchain technology? In this article, we’ll break down the basics of hashing and its role in securing blockchain technology, as well as explore how it keeps data safe. We’ll also address related questions like how a block of data on a blockchain gets locked. and since blockchain technology is public, how are the identities of users protected? Whether you’re a beginner or a seasoned tech enthusiast, this guide will help you understand the key principles of blockchain security.
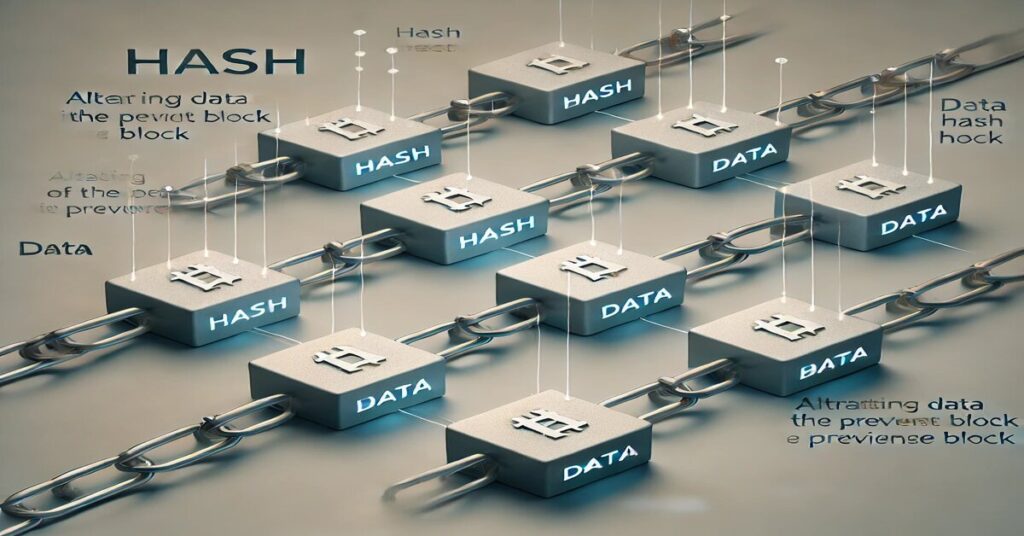
What Is a Hash and How Does It Work?
Let us begin with the fundamentals of hashing in order to comprehend how a hash aids in the security of blockchain technology. When data is entered into a hash function, a unique string of characters called a hash is produced. For that data, the output, or “hash value,” functions as a digital fingerprint. The input changes even little, and the result is a completely different hash.
When “Hello Blockchain” is processed through a hash function, for example, the result could look like this: 2cf24dba5fb0a030e. But altering just one character will produce a totally different hash, such as 3d23fdb04a9c1db2.
Crucial Elements of a Hash
- Fixed Length: The hash will always have the same length regardless of the volume of data.
- Uniqueness: The hash value of each unique input varies.
- One-Way Function: From the hash, it is almost hard to reconstruct the original data.
These characteristics—uniqueness and immutability—are essential to blockchain technology because they guarantee that data added will never be changed without detection.
How Does a Block of Data on a Blockchain Get Locked?
One frequently asked issue is: how does a blockchain data block become locked? This entails hashing the data in the block and tying it to the hash of the block before it to create a safe chain. Here’s a quick, step-by-step explanation:
- Gathering of Data: Miners gather a group of transactions to create a block.
- Hashing the Block: A hash function is applied to the block’s contents to get a unique hash.
- Linking to Previous Block: To establish a safe chain, every block has a hash of its own as well as the hash of the block before it.
- Proof of Work: To answer challenging riddles, miners must modify a nonce to satisfy particular requirements, which locks the block in place. This is a computationally demanding procedure that is hard to change.
Because of this interlinking, the system as a whole is protected against tampering because any changes made to one block will need a recalculation of all future blocks.
Since Blockchain Technology Is Public, How Are the Identities of Users Protected?
One of the most frequent worries is how user identities are safeguarded, given that blockchain technology is open to the public. This is where public-key cryptography and cryptographic hashing are useful.
Keys, both public and private: Every user has a private key, which functions as a password, and a public key, which functions as a username. The public key is used to record transactions, guaranteeing the privacy of personal information.
Hashing to Maintain Anonymity By converting user data into a cryptographic hash, hash functions ensure that the transaction records are not the only source of information used to uncover the true identity of the user.
For instance, if Alice pays Bob two Bitcoin, the transaction is hashed and published on the blockchain using their public keys. The real names behind those public keys are kept a secret in order to protect privacy and guarantee openness.
What Best Describes the Relationship Between Blockchain Technology and Cryptocurrencies?
It is essential to comprehend how blockchain technology and cryptocurrencies are related. What then sums up the connection between cryptocurrencies and blockchain technology the best? Here’s an easy comparison:
- Blockchain as the Basis: A decentralized ledger, made possible by blockchain technology, is used to log transactions. It guarantees immutability, security, and transparency.
- The Use of Cryptocurrencies: Digital currencies that function without a central authority are known as cryptocurrencies, and they include Bitcoin and Ethereum. These currencies are powered by blockchain technology.
Consider blockchain as a railroad track, with cryptocurrencies acting as the train that travels on it. Cryptocurrency is the train, and the track (blockchain) makes sure it travels safely and straight forward.
What Is a Digital Asset?
Digital assets are becoming more and more important in a world that is becoming more and more digital. Is a digital asset, though?
Anything with a monetary or social worth that exists in a digital format is referred to as a digital asset. Digital art, data, NFTs (Non-Fungible Tokens), and cryptocurrency are a few examples. Since these assets are often traded and kept on blockchain platforms, the security and transparency of their ownership records are guaranteed.
Example of Digital Assets in Action:
Consider purchasing an NFT for a digital painting. A blockchain is used to store the history of this purchase, including your ownership. This data is secured using the hash function, which makes sure it cannot be changed and demonstrates your ownership.
The Role of Hashing in Securing Blockchain Transactions
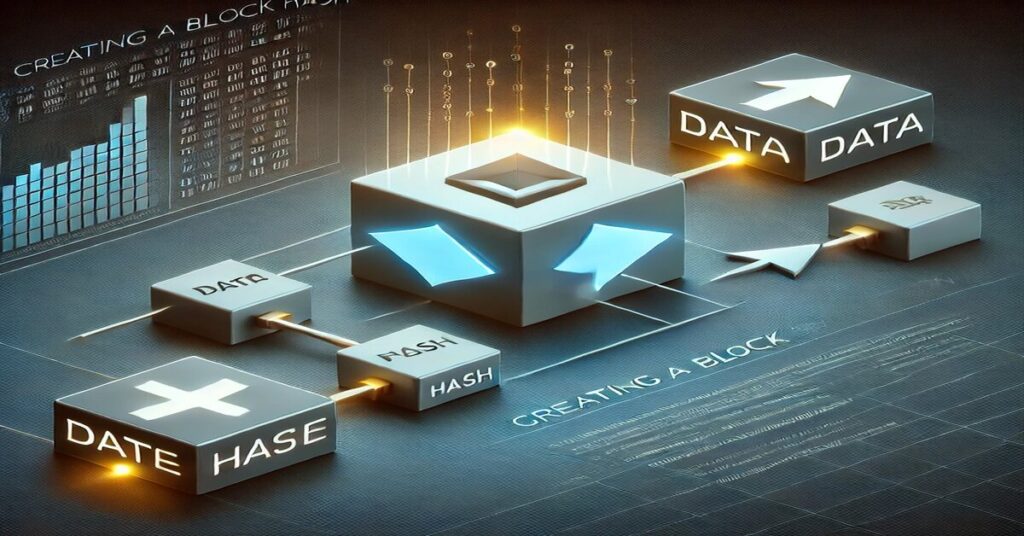
How does a hash help secure blockchain technology? Let’s dive into the role of hashing in securing transactions:
Step-by-Step: How Hashing Works in Blockchain Security
- Recording a Transaction: A transaction is hashed after it takes place.
- Combining Transactions: To enable speedy individual transaction verification, several hashed transactions are merged into a Merkle tree.
- Creating a Block Hash: A block’s hash is generated by hashing its transactions and the hash of the previous block.
Blocks are securely linked together when the block hash is appended to the subsequent block.
- Proof of Integrity: Tampering is easily detected because any modification to the transaction data will affect the block hash.
Blockchain is made secure by this method, which also guarantees that a transaction cannot be altered once it is recorded without also changing all subsequent blocks, making the effort nearly hard without a lot of processing power.
Storytime: How Hashing Prevented a Digital Heist
Suppose you have a digital wallet that is brimming with cryptocurrency. A hacker tries to change your transaction history one night in an attempt to take money from you. However, due to the nature of hashing and blockchains, any attempt to modify even a single transaction would modify the hash of that block, which would then modify the hash of every subsequent block in the chain.
Recalculating the block hashes would take so much work that it would be equivalent to attempting to rewrite a bank’s whole record history in a single day. Your money is safe since the hacker gives up because of the effectiveness of cryptographic hashing.
Conclusion: Why Hashing Matters for Blockchain Security
Finally, how does a hash contribute to security? The main goal of blockchain technology is to safeguard data in an environment that is impenetrable to tampering. Block manipulation is practically impossible, data integrity is guaranteed, and user identities are kept anonymous with the use of hashing. Hashing will continue to play a crucial role in preserving security and trust in a decentralized society as blockchain technology develops.
Hashing is the key to understanding why blockchain is said to be so secure, whether you’re wondering how a block of data is locked or how blockchain relates to cryptocurrency.